OSCP Progress
I’ve been very busy and haven’t been posting for a while. I wanted to share a lot with you guys, but literally had no time or was probably exhausted to even think about blogging. However, finally, I found some time to post about the stuff that I’ve been doing and will try my best to keep posting some interesting stuff. So for today, let’s talk OSCP.
Introduction
For those who don’t know, OSCP is a hands-on offensive information security certification. Moreover, it is a willingness to forget about sleep for a month, willingness to learn the hard way, cursing a lot, and becoming humble at the end.
My Progress
I started my OSCP labs 16 days ago. So far it has been quite an adventure. I hate it and I love it. There are 44 machines in Public network, and I also got access to IT network where there are 6 more horny boxes that are just waiting to be pwned. I am working on exploiting machines whenever I have a chance, mostly during the evenings and over the night too on some weekends. I have rooted 23 machines so far out of the 50 that I have access for. These 23 machines also include Pain, Gh0st, Sufference, and Humble. The latter 2 are the ones that kept me up over night on those weekends. However the feeling when I rooted them was amazing! :D I must admit, that getting low privilege access on those two (Sufference and Humble) was even more satisfying than getting root. Sufference took me about 20 hours to get root and Humble took about 10 hours. The pain and ghost were fun but relatively easy, and each probably took me about 30 minutes to get root.
During these 16 days I wrote my own enumeration scripts that are lightning fast and are becoming part of a larger tool that I probably (unfortunately) won’t be able to share, since too many parts of the code are also being implemented at my job, therefore can’t publish it in accordance to the IP policy of the company.
During these 16 days I also wrote my first MSF module to a certain exploit that doesn’t have any coded scripts that script kiddies could use, however when I asked Offensive Security team for a permission to publish it, they kindly asked not to. :D
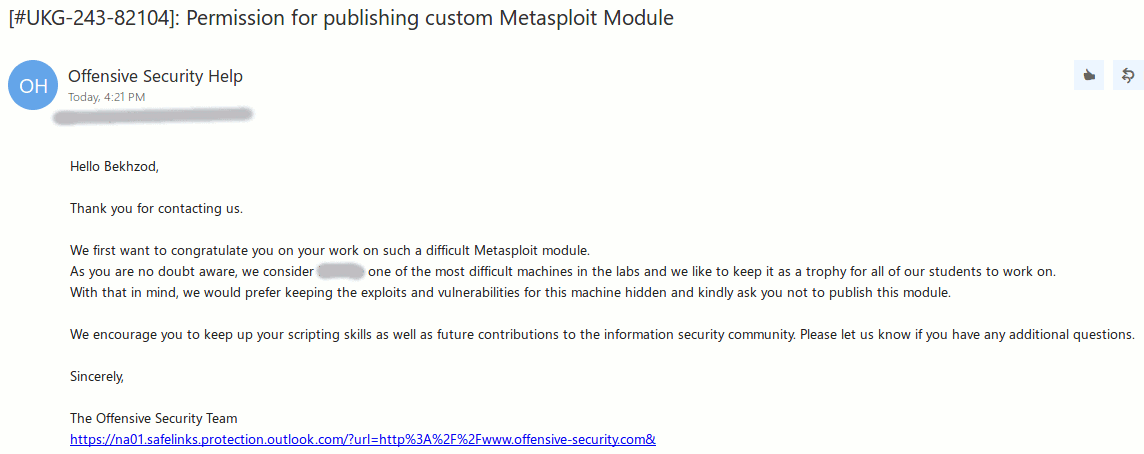
I understand their position and respect their request.
Besides writing custom toolsets, I also learned a lot on tons of things that I had never thought existed.
I am planning on rooting at least 20 more boxes till the end of this weekend, because according to my calculations I am far behind the schedule as I only pwned 23 machines in 16 days whereas I should have had 32 (16days * 2 machines per day) in order to be able to pwn all machines within the allocated 30 days of lab time. I think sufference and humble kinda threw me off the schedule too. So now I am trying as hard as possible to catch up with my own schedule and complete all the machines before I hit the day 30.
Thoughts
I recommend taking the course for everyone who’s thinking about going into Cyber Security field or whoever is in the field but doesn’t have the certificate yet. You will love it and you will learn a lot. Even if you fail it, the learning experience you get from it is unforgettable.