Exploiting MuraCMS
I have mentioned in my last post that I have been waiting for a responsible disclosure deadline (90days) to expire on one of the projects I’ve been working on. It finally did and here is the whole story.
Update
CVE ID: CVE-2018-7486
Assigned: 02/26/2018
URL: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-7486
Background
Mura CMS is open source Content Management System that is powered by ColdFusion Markup Language (CFML). It is used by quiet large organizations. For the full list of organizations that use Mura CMS follow this link.
Vulnerabilities Identified
All vulnerabilities were identified in Mura CMS < v7.0.7029
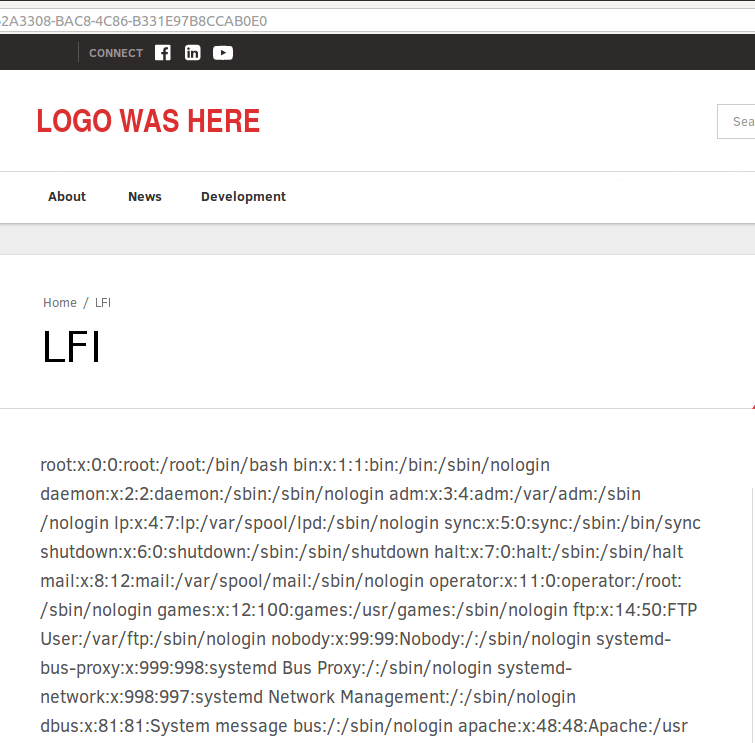
Issue 1: Local File Inclusion (LFI)
Identified: 09/06/2017
Privileges Required: Administrator
Description: Vulnerability in Mura CMS content editor allows for local file inclusion.
Issue: Mura’s functionality to include Mura functions inside the content editor using [m][/m] tags by default gives an option to include “.cmf” files using “$.dspInclude()” and “$.dspTemplateInclude()” functions. Both these functions are relative to the path of the app location and are vulnerable to directory traversal as well as local file inclusion without checking for the file extension.
Example: [m]$.dspinclude("../../../../../etc/passwd")[/m]
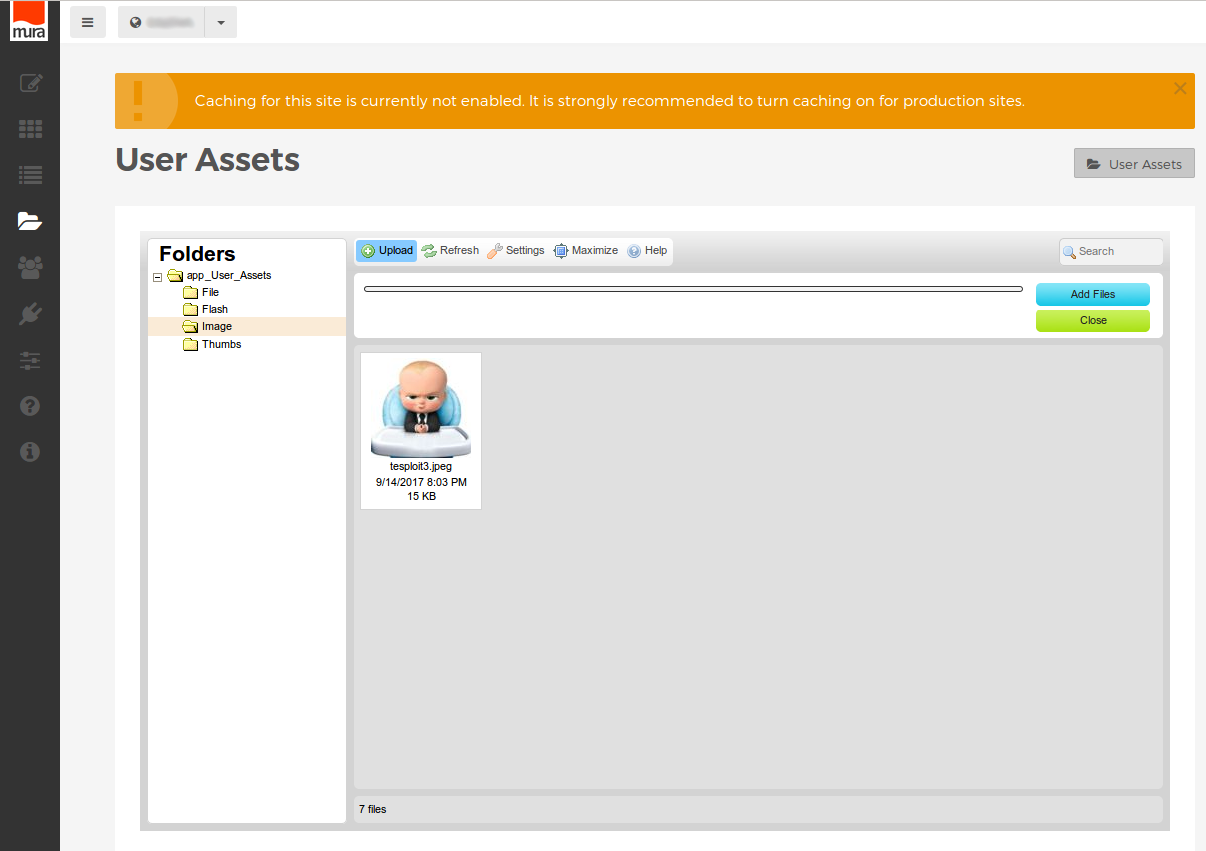
Issue 2: Uploading Files With Malicious Content
Identified: 09/14/2017
Privileges Required: Administrator
Description: CKFinder plugin in Mura CMS allows for uploading image files with malicious content.
Issue: CKFinder filters all files being uploaded for file extensions and mimetypes. However, it is still possible to upload an actual image file containing malicious CFM code.
Example:
Issue 3: Remote Code Execution
Identified: 09/14/2017
Privileges Required: Administrator
Description: Using the above found vulnerabilities it is possible to exploit RCE on Mura CMS
Issue: Uploading an image file using CKFinder, then including this image file in content editor using either $.dspInclude() or $.dspTemplateInclude() functions will force the image file to be read as regular file. This will result in malicious content inside the image file being rendered as part of the Mura app content.
Example: Following images show step by step process of exploiting RCE vulnerability. This example shows only one way of remotely executing commands on victim machine using found vulnerabilities.

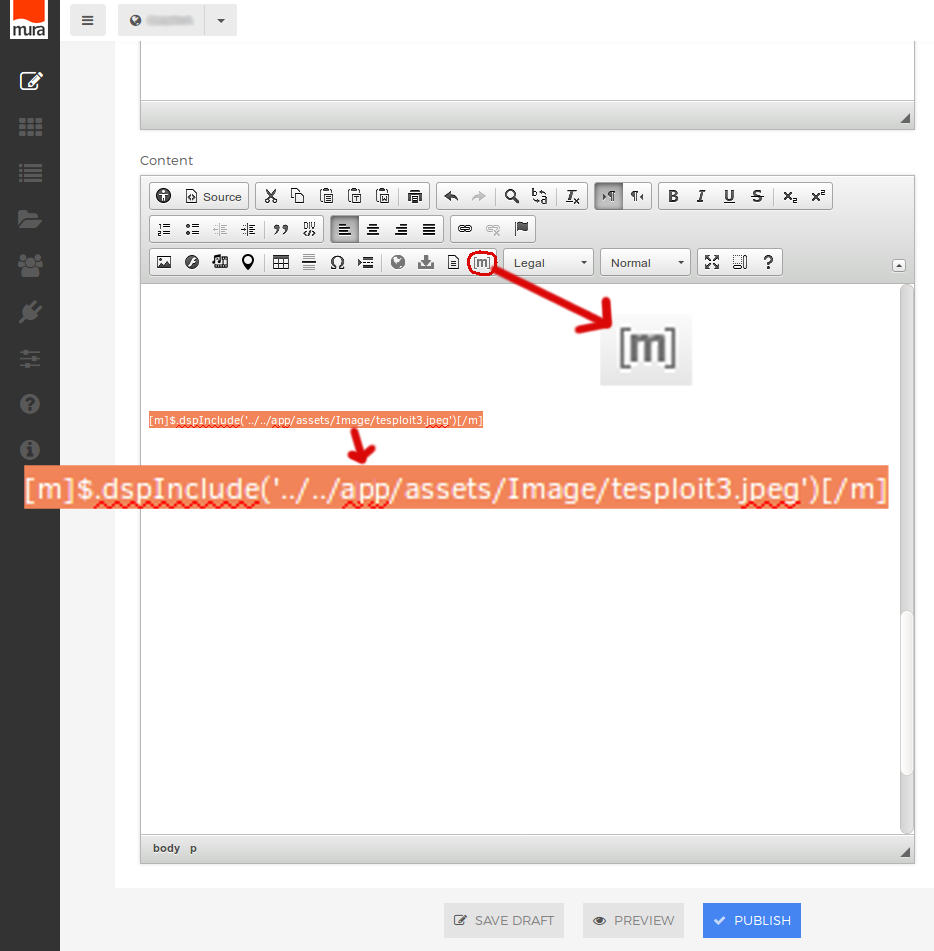
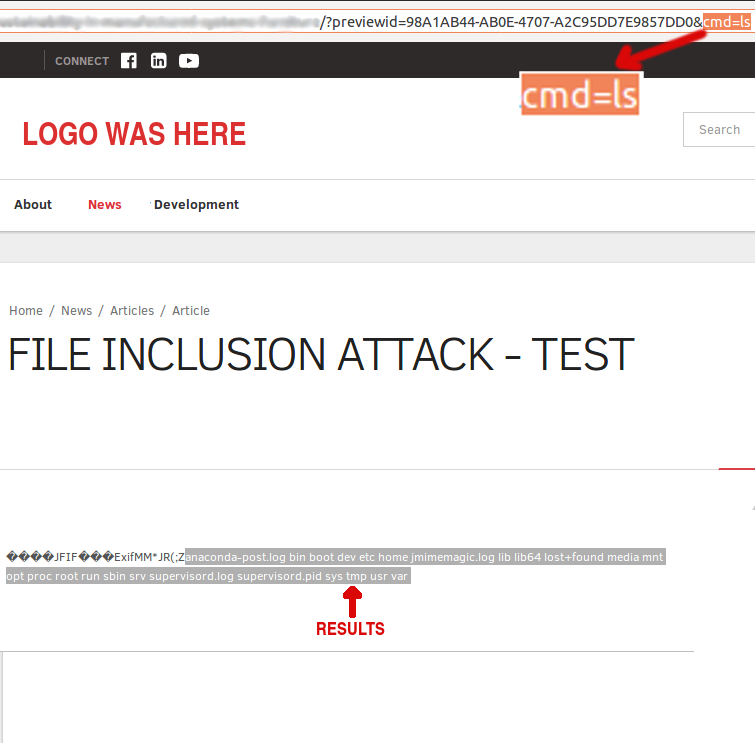
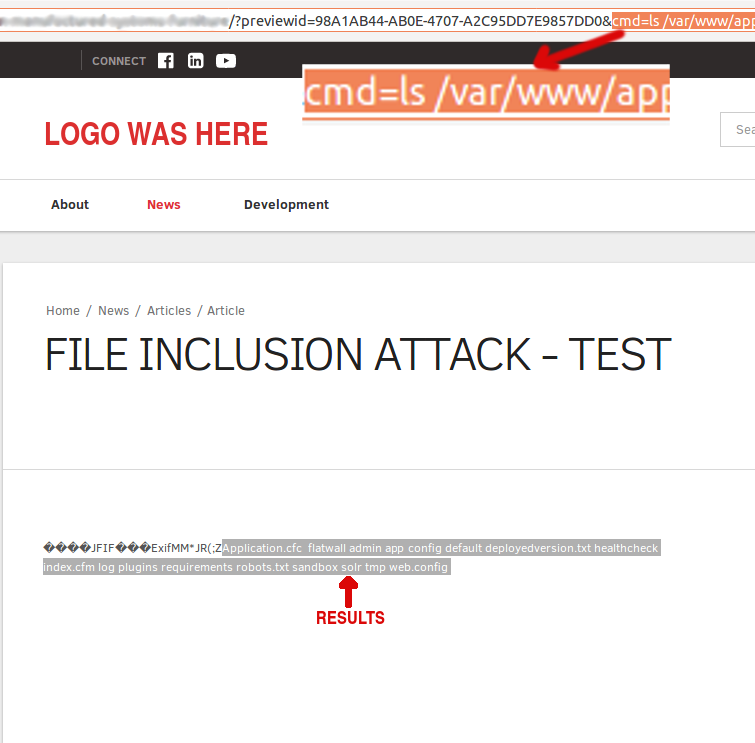
Chronology: Contacting BlueRiver
Reported to BlueRiver: 09/20/2017
BlueRiver fix: 09/29/2017
- Limited file types
- Sanitized file types
Test of mitigations: 10/02/2017
- File upload still exists
- RCE still possible using other file types (tested .txt and .pdf)
BlueRiver fix: 10/12/2017
- Removing mura tag in test environment fixed the LFI, hence the RCE
- File upload still exists
Report on mitigations: 10/12/2017
Mitigation
Update to latest version of MuraCMS
The best solution provided by BlueRiver on issues found was to remove mura tag from content editor to fix the RCE. BlueRiver also sanitized file types used during the test for Issue #2, however since it is hard to sanitize every single file type, it is best to limit CKFinder to upload only those file types that are sanitized by BlueRiver. If you need to use other types, then it is best to disable Mura tag in your Mura CMS configuration.